Smartest Details for the Perfect Password Hashing
The time window for changing passwords before the hackers manage to go back up by decrypting our hash string is very short a matter of a few days, if not a few hours; if the SHA1 is strengthened by bcrypt, then users have much more time to change credentials and, eventually, close their accounts. It’s the Authentico option for you.
What is hashing
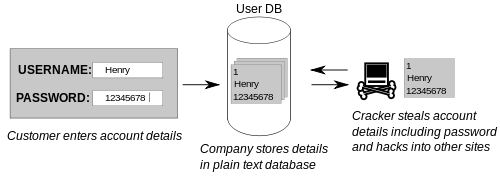
It should be remembered, in fact, that in case of a data breach, theft of databases with credentials by hackers, it is necessary for the user to change the password not only of the compromised profile but also of the others. Only in this way, in fact, can you be sure that your data is safe. To verify that you have not been a victim of identity theft, you can use the portal, you enter your password, and it turns out if by chance it is already part of one of the databases stolen by hackers over the years.
How to hack password hashing
As experts himself states, hackers who are able to decode hashes are neither sorcerers nor even black magic. They simply have a lot of patience and are equipped with extremely powerful computers or botnets. Once the database has been stolen with the credentials defended by SHA1 and bcrypt, they exploit the computing power of the GPU to try to trace the initial passwords in the clear.
Hacker hashing
At their disposal, in addition to an adequate hardware compartment, they have real dictionaries composed of words of complete meaning and hash algorithms used by the same web service providers. By feeding the dictionaries of various languages to these algorithms and comparing the results obtained with the entries in the stolen database, they are able to trace the passwords, in this case, meaningful words in some known language and use them for their purposes. Alternatively, they exploit already compiled lists, composed of a hash of sentences and random alphanumeric character sequences, to then be compared with the elements that make up the database obtained fraudulently: in this case too the hackers will be able to find the correspondences between the hash of the string and go back to the clear passwords. At this point, using the data obtained or selling the results to the highest bidder becomes child’s play.
Chess game
Computer security experts, of course, are not watching. As if you were in a real chess game, the attempt to attack the hackers corresponds to the defensive move by the companies that defend users’ credentials. So, to make the challenge more compelling, they add some salt to their password hashing algorithm.
The salting technique consists of adding random and useless information to the password before hashing and then storing it in the database. In doing so, even if a hacker were to succeed in taking possession of the list of user access credentials, they could do us very little since the hash created would not exactly match the users’ password but only one of its sweetened versions.
Techniques such as bcrypt and Argon2, on the other hand, make the storage of credentials safer by performing thousands of steps through different hashing algorithms: in this way the deciphering operations are prolonged a lot, thus making it impossible or really very long the password cracking process.
